Microsoft’s Cloud Solution Provider program is a great option for service providers that provide managed services on Azure. It enables the partner to provide a single bill encompassing both cloud services costs and managed services costs to the customer. There are scenarios where the customer may have purchased Azure through another licensing channel and wants the service provider to take over management of the environment. For CSP partners, they can leverage the existing identity model that CSP provides to manage Azure subscriptions provisioned through other licensing channels. This is enabled by establishing a reseller relationship with the existing tenant and then assigning permissions to the appropriate group in the partner’s AAD tenant.
- Log in to Partner Center using your admin CSP credentials and generate a link to establish a reseller relationship from Dashboard > CSP > Customers > Request reseller relationship.
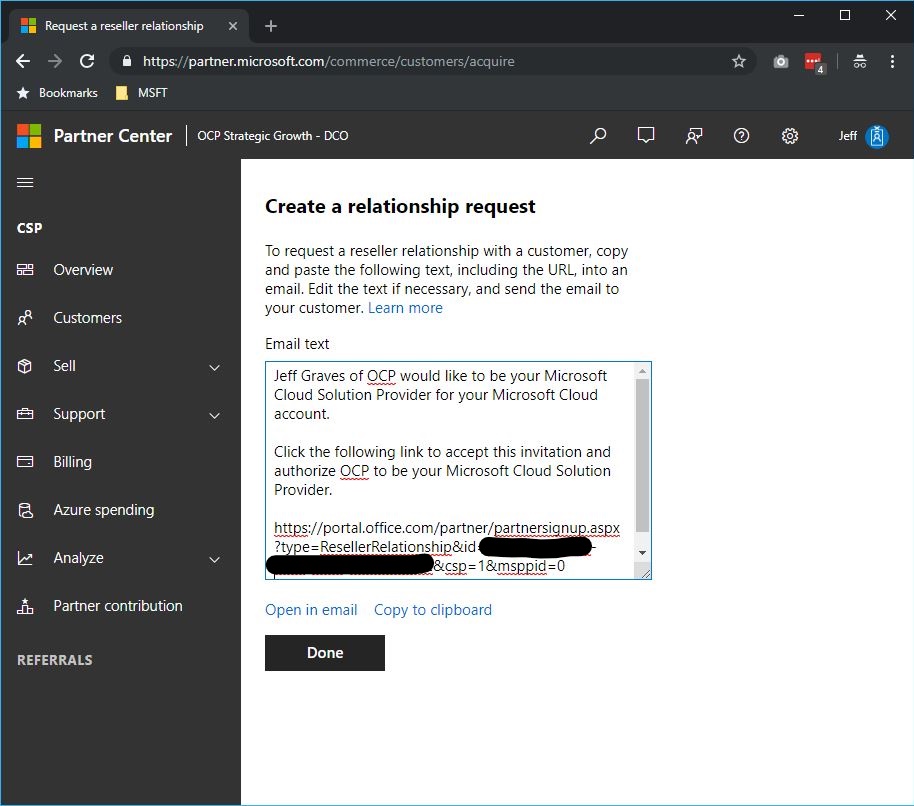
- Send the link to the customer to have them accept the invitation and authorize the CSP relationship.
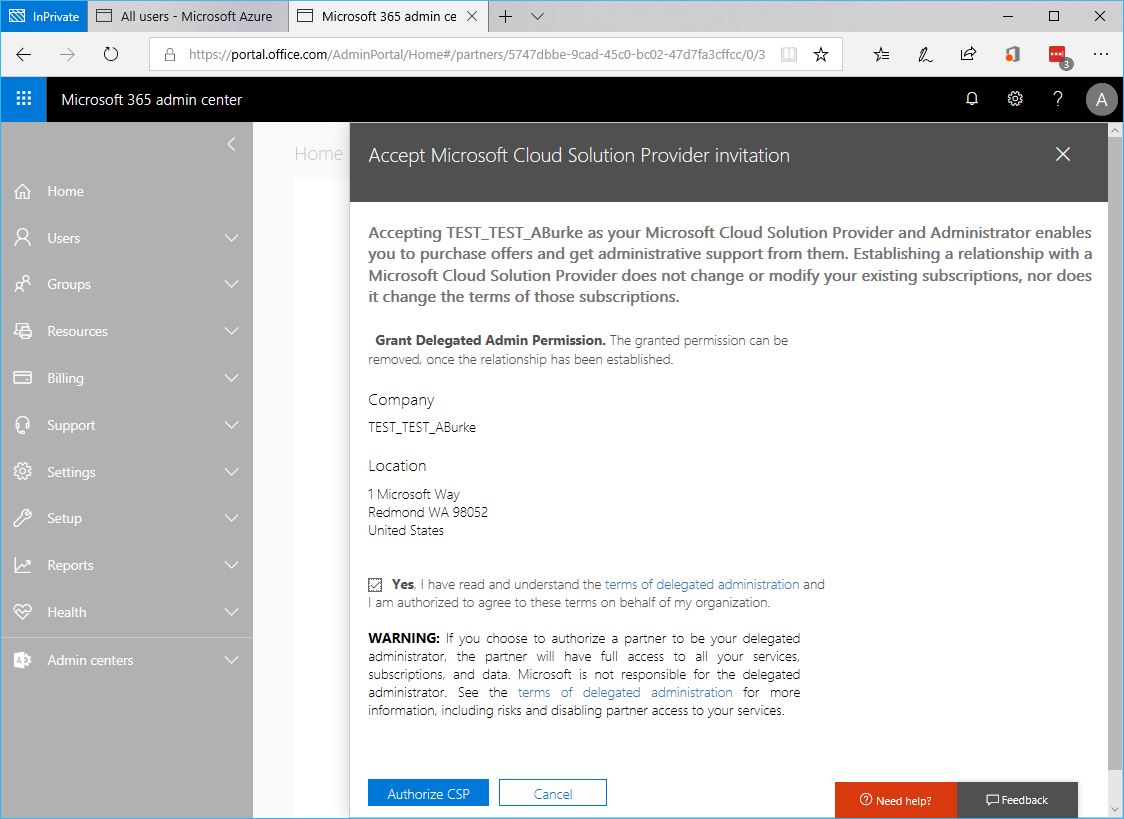
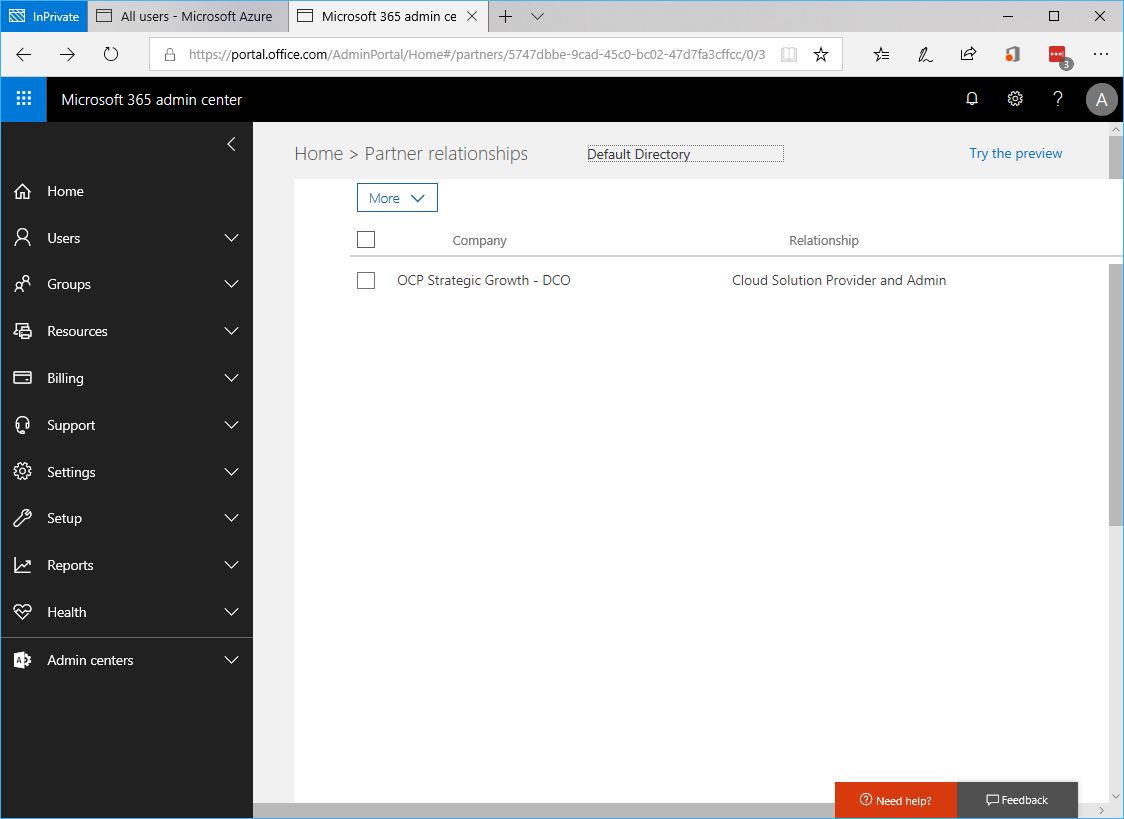
- Once authorized, the customer can see the Partner in Admin Center under Partner Relationships
- As a partner, you will now find the customer in your Customer List in Partner Center under Dashboard > CSP > Customers.
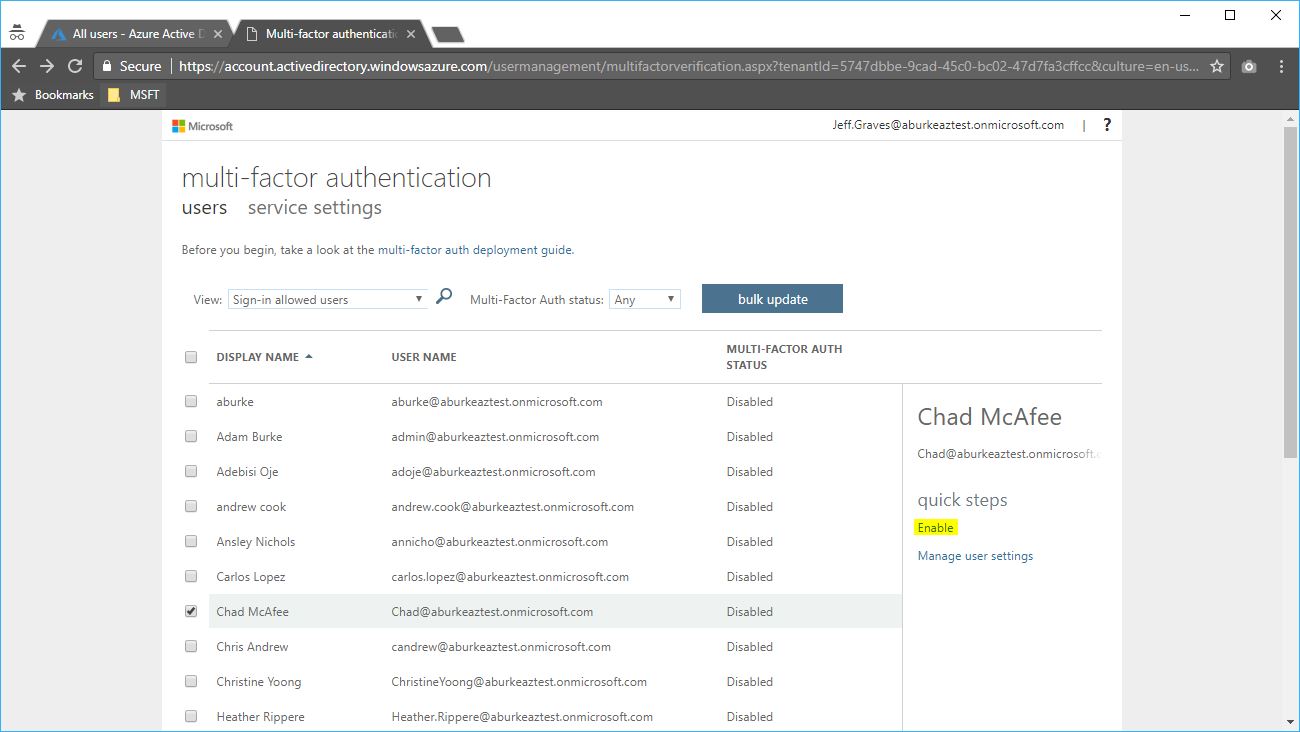
- Open the Azure Active Directory Admin Center, browse Groups and select the group you want to have access to the customer’s subscription (note: You must select either AdminAgents or HelpdeskAgents groups). Copy the Object ID of the group.

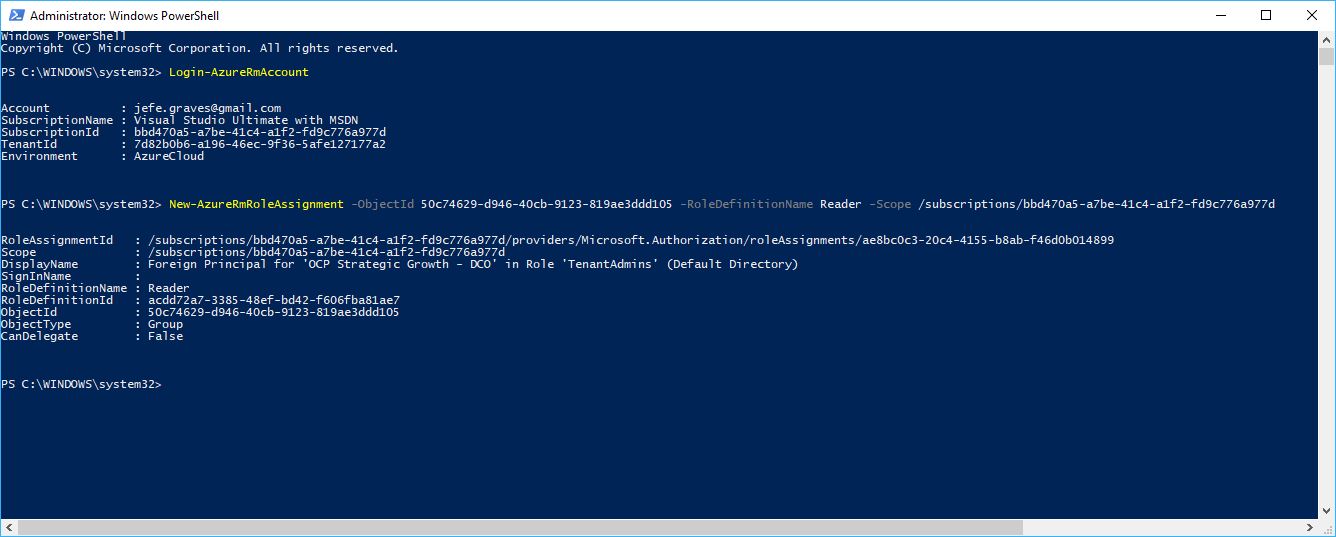
- Using PowerShell, an existing admin in the customer’s subscription will need to grant the partner’s group permissions to the subscription using the New-AzureRmRoleAssignment cmdlet. Permissions can use any Role Definition (ie. Reader, Contributor, Owner) in the customer’s subscription and can be scoped appropriately (ie. Subscription, Resource Group, Resource).
New-AzureRmRoleAssignment -ObjectId 50c74629-d946-40cb-9123-819ae3ddd105 -RoleDefinitionName Reader -Scope /subscriptions/bbd470a5-a7be-41c4-a1f2-fd9c776a977d
- The partner can now use the link to the Azure portal from Partner Center to manage the customer’s subscription.

- The partner can also manage the subscription using PowerShell by using the TenantId parameter.
Login-AzureRmAccount -TenantId 7d82b0b6-a196-46ec-9f36-5afe127177a2